Over the last 8 years the number of websites using WordPress has increased from 13% to 31%. While it hasn’t completely dominated the internet yet, WordPress use has grown consistently by 2-4% every year, and it is the most popular content management system (CMS) in use. As a WordPress user, this is good news and bad news. The good news is that with so many users, there is a strong community dedicated to the improvement and development of the CMS. The bad news is that with so many users, WordPress sites are often targeted by hackers.
1Ignoring WordPress and WordPress Plugin Update Notifications
Keeping plugins up to date is the most important thing you can do to keep your website safe.
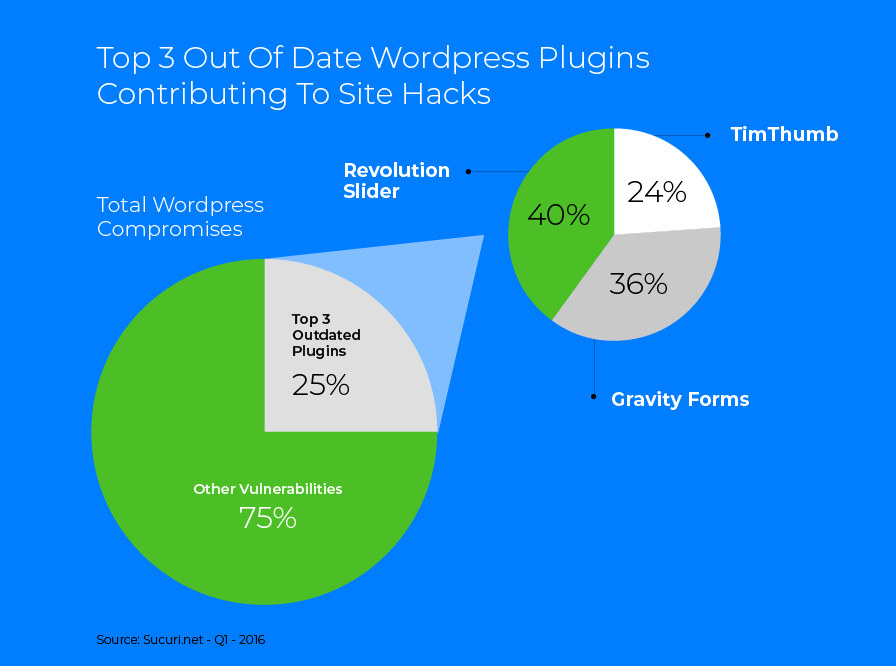
It’s easy to ignore the notifications when you log in to your website, but every time you put it off, you are putting your website in danger. Hackers search for known vulnerabilities in plugins and old versions of WordPress and then scour the web to find websites using those old versions. Sucuri.net reported that 25% of the websites they cleaned were exploited through three popular WordPress plugins – all of which had available updates that could have prevented the websites from being hacked (Q1, 2016).
Keeping your website up to date is easier said than done. Updating WordPress core files can cause plugin compatibility issues. Updating plugins can “break” your website. Before you update anything, make sure you have your site backed up.

PRO TIP: Keeping WordPress up to date is much easier if you have a staging environment for your website. In a staging environment you create a private copy of the latest version of your website. This allows you to update your WordPress and plugin files and test the effects without affecting your live site. Once you are sure everything is compatible and your site is working as expected, you can copy the files from your staging environment over to your live website.
2Storing Website Backup Files where your Website is Hosted
If you don’t know if, how often, or where your website is being backed up, you should find out – NOW. Backups can save you thousands and thousands of dollars in website cleaning and recovery fees.
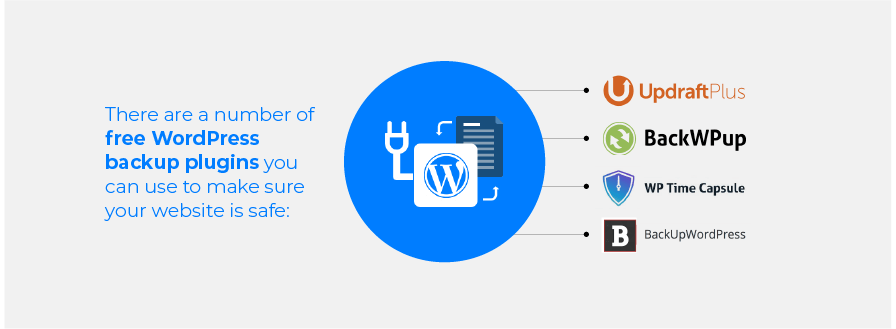
There are a number of free WordPress backup plugins you can use to make sure your website is safe:
The safest way to store your backup files are to save them to an alternate server location like Dropbox, Google Drive or Amazon. If your website comes under attack, your backup files saved on a different server will be safe from infection. Depending on how your backups are setup, you will probably still want to keep a backup on your website server for easy backup creation and restoration when your website is affected by user error (e.g. accidentally deleting something). Creating a local backup before doing any website editing is excellent protection against user error.

PRO TIP: If you don’t have a backup and your site ends up being hacked, contact your website host before you pay for a cleaning service. Some website hosts take backups of all of their hosting space regularly and will offer restoration from their backups for a fee. It may not be the most current version of your site, but it may be a cheaper option than having your site cleaned.
3Using the Default WordPress Username
One of the most popular ways for a hacker to gain access to your website is by using a “Brute Force Attack”. This kind of attack involves a hacker finding your login page and using software to try and “guess” your credentials. If you are using the default “admin” username that is recommended during the WordPress setup, you are cutting their work in half!
- Always use unique usernames coupled with strong passwords
- Never create more logins that you need
- Don’t assign more permissions than necessary to each user
- Delete unused or obsolete logins

PRO TIP: Installing a good security plugin like Wordfence can help protect against brute force attacks and many other vulnerabilities. Security plugins help protect you by limiting login attempts, enabling two factor authentication, and blocking known blacklisted IP addresses.








Sorry, the comment form is closed at this time.